Security Groups - Intermediate
Lesson 10
You know what a security group is and how to deploy one with Terraform. You can add multiple ingress rules and understand the ports and protocols used. In this lesson, you’ll be expanding on your knowledge by learning how to associate one of the EC2 instances you created with the security group you created. This means any traffic that wants to access your EC2 instance must first get through your security group.
As your EC2 instances stand now, they are publicly accessible by anyone, from anywhere, through any port. Putting your EC2 instance behind a security group is one way to control the type of traffic (and where it comes from) that can access your EC2 instance.
Currently, you have three ingress rules for your security group:
ingress {
description = "Inbound insecure internet traffic"
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
This ingress rule allows
insecureinternet traffic in throughport 80from anywhere (["0.0.0.0/0"]).
ingress {
description = "Inbound insecure internet traffic"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
This ingress rule allows
secureinternet traffic in throughport 80from anywhere (["0.0.0.0/0"]).
ingress {
description = "allow ssh from my computer"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["96.7.151.52/32"]
}
This ingress rule allows
sshtraffic in throughport 22from your computer (["96.7.151.52/32"]).
If you put your EC2 instance behind this security group, it will no longer be completely open, but instead can only be accessed over the internet through port 80 or 443, or from your computer via ssh. It might not seem like it yet, but this makes your EC2 instance incredibly more secure than it was before.
Let’s jump in and start building!
Table of contents
- Security Groups - Intermediate
- Referring to other terraform resources
- Connect an
EC2 instanceto thesecurity group - Change the name of your
security group - Next Steps
Referring to other terraform resources
In AWS, most of your resources are working together or are, in some way, connected. You will almost never have an EC2 instance running alone in an account, completely separate from other resources. You’ll want to do things like put it behind a security group, in a specific VPC or subnet, or have it use a particular launch template (don’t worry, you haven’t learned about any of these yet). In AWS, if you wanted to put your EC2 instance behind a particular security group, you would navigate to the instance in AWS and click the security group you want from a drop down menu. It would be manual work everytime you needed to change the security group.
You can do the same thing in Terraform, but without the manual work. Once you have the code set up, it’s there to stay. In your current ec2-terraform project you now have two EC2 instances and a security group, but they haven’t yet been connected – they are still completely separate from each other.
Given the current rules for your security group resource, and the knowledge that:
- Your
front-end EC2 instanceshould be accessible via the internet - Your
back-end EC2 instanceshould not be accessible via the internet
Which EC2 instance do you think you will be associating with your security group?
Answer
The front-end EC2 instance!
The current ingress rules for your security group allow both insecure and secure internet traffic (http and https, respectively). As your
front-end EC2needs internet access (and yourback-end EC2doesn’t), you will be associating thefront-end EC2with the current security group.
We are going to use the above example to demonstrate how you can connect different resources you create together. This will become incredibly important later on as we build more and more resources that need to be connected. You should complete this lesson as many times as it takes for you to feel confident in the process.
Connect an EC2 instance to the security group
Currently, you have an ec2.tf file, which contains two EC2 instances and a security_group.tf file, which contains a single security group. Right now, they are separate resources that aren’t associated in any way.
Let’s change that!
For now, we just need the id of the one security group we’ve created. We have two options to get it:
- We could log in to AWS, find the security group, copy the id, then paste it into the security_groups list, OR
- We could refer to the security group directly in terraform, without needing to go find the id in AWS.
The first option isn’t ideal because everytime we would have to first run
terraform applyto create the security group, then do all the manual work of finding the newly createdsecurity group id, then go back into terraform, paste in the id, then runterraform applyagain. We would have to do this process any time we needed to launch our whole stack for a new client or new application. Not ideal.The second option takes out all the manual work! If we refer to the security group we create in terraform (instead of the id it will have once deployed) terraform will automagically associate the two!
- Open up the
ec2.tffile. - For the
front-endEC2 instance, add a new parameter:security_groups. The parametersecurity_groupsaccepts a list of strings. This means you could list the ids of multiply security groups if you wanted to. - To associate resources in terraform, you will use similar syntax every time. In the
security_groupsparameter, start typing:aws_and see what autocomplete options show up. - You should notice that you have two options:
instanceandsecurity_group. This is because your code editor scans your terraform code and looks for the resources you have. This scan shows that you have at least oneinstanceresource and at least onesecurity groupresource. - We want to associate our
security_groupso choose it from the dropdown. - Then type
.and see what autocomplete options you have. Now, you will need to choosewhichsecurity group you want to associate. Because you only have one security group, you only see one option right now:yourname-security-group. - Choose
yourname-security-groupfrom the options and type.again. You will see a long list of autocomplete options. - Now, you need to decide
what informationabout the security group you need: thearn,name,id, etc. In this case, you need thename, so choosenamefrom the options.Note: In most cases, you will need the
idof a resource, but sometimes you will need other identifiers, such as thenameorarn(similar to anid). In this course, we will always tell you what you need, but you can also find it for yourself by searching through the Terraform docs (a topic we will also cover later). You need thenamecurrently, because your security group and instances are deploying into adefeault Virtual Private Cloud (VPC). Once you create your own VPC, we’ll switch this reference toid. - You’re done! You’ve now told your
front-endEC2 instance it needs to be “behind” the security group you’ve created (yourname-security-group). - Run
terraform apply, log in to AWS and verify yourfront-endEC2 instance is associated with the correct security group.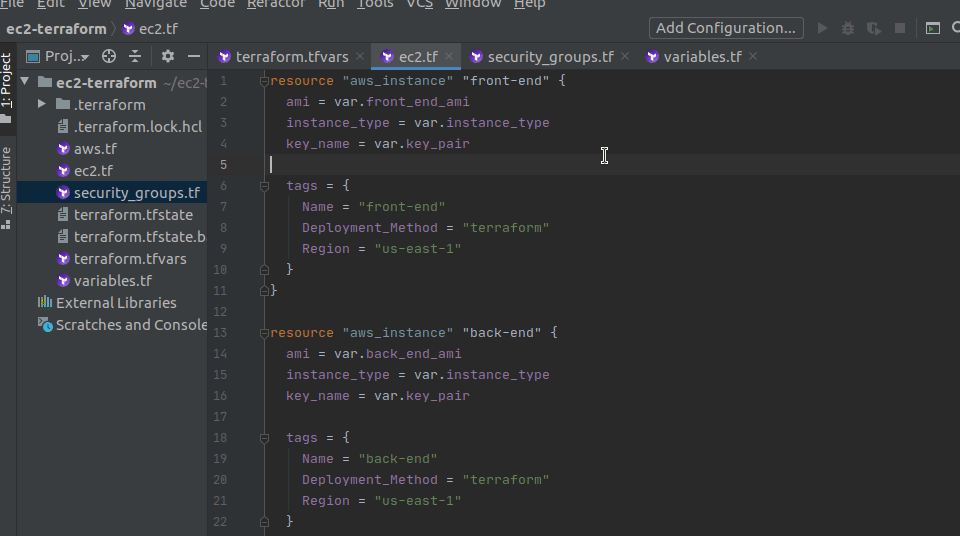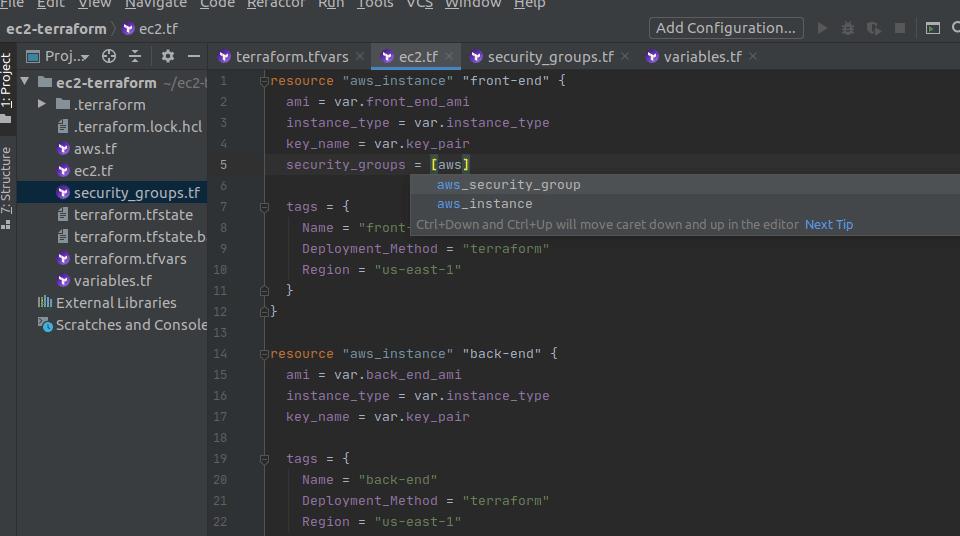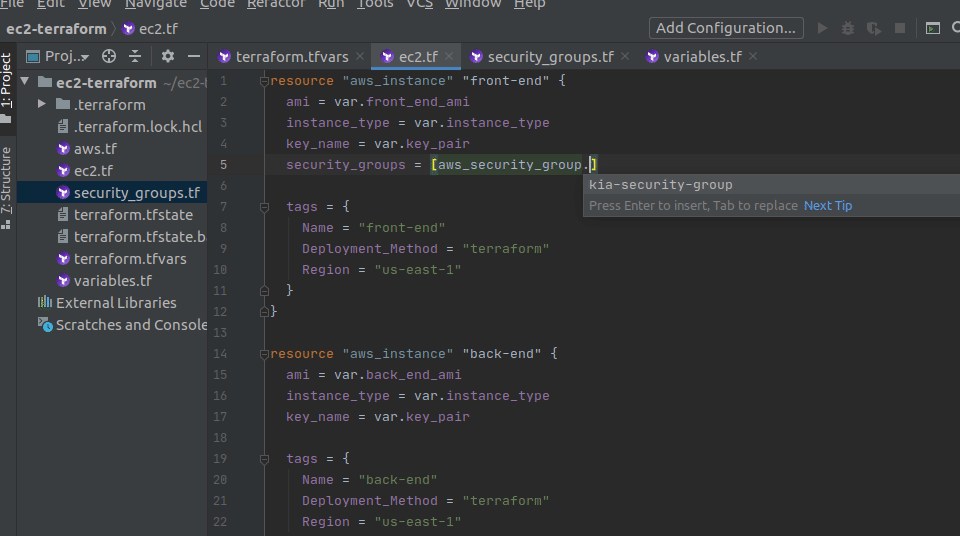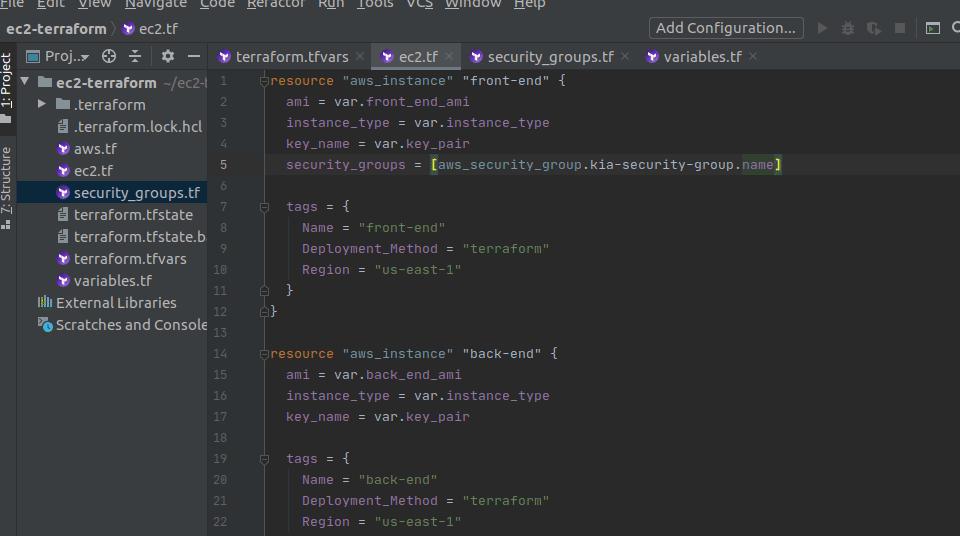

Change the name of your security group
Change the name, then go back and re-associate.
Next Steps
You’ve now covered what type of EC2 instance would go behind the security group you have created and how to associate resources in Terraform. How you feel about referring to resources and why you associated your front-end EC2 to your security group determines what you should do next.
Redo the lesson (optional)
If you don’t feel as comfortable as you’d like with the above lesson, you can start over.
In your
ec2.tffile, simply delete the line:security_groups = [aws_security_group.yourname-security-group.name]
You’ll then be back to where you started! Head to the beginning of the lesson.
Move On
Once you understand:
- How to associate a resource in Terraform with another resource
- How to update names of resources
- Why having ingress rules for ports 80 and 443 mean only the
front-endinstance should be associated
You should feel confident moving on to the next lesson, Advanced Security Groups.